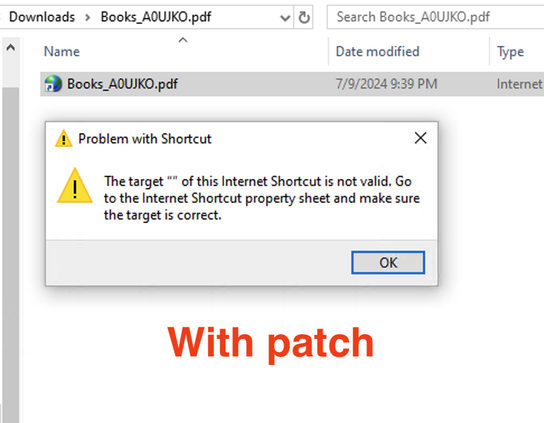
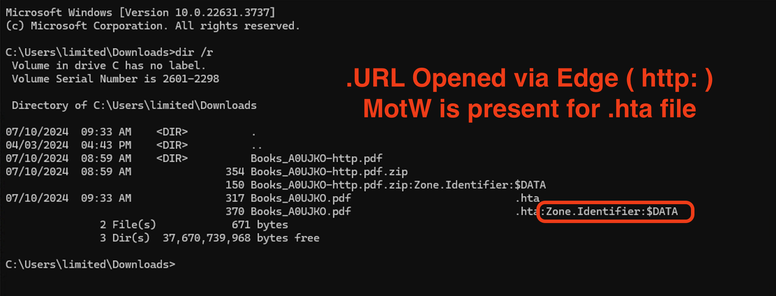
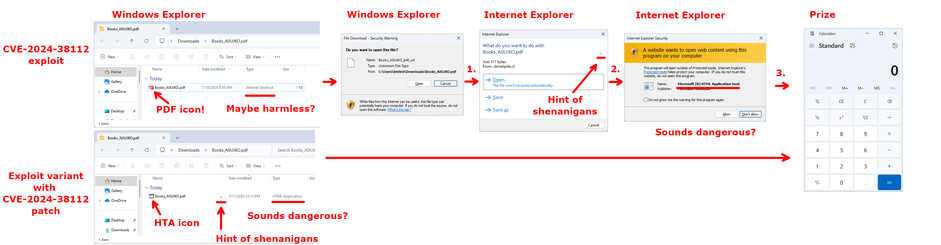
Microsoft CVE-2024-38112 being exploited ITW, discovered by Haifei Li, is sort of neat. It uses the gift that keeps on giving, the MHTML: URI handler to force IE to open web content. With the update, Windows no longer recognizes mhtml: URIs in .URL files anymore.
What's the significance of having something open up in IE vs. Edge?
IE is way more YOLO about how it does things with Windows.
First, IE will allow you to download a .HTA file from the internet without warning.
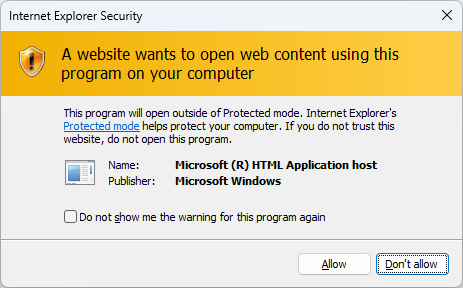
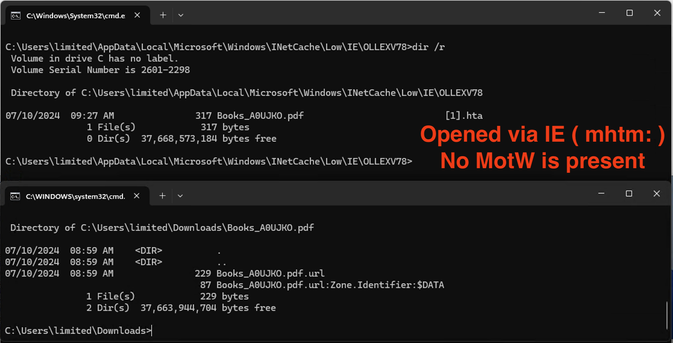
Next, once it's downloaded, the .HTA file will live in the INetCache directory, but it will NOT explicitly have a MotW. At this point, the only protection the user has is a warning that "a website" wants to open web content using a program on the computer. Without saying which website it is. If the user believes that they trust "this" website, this is when code execution happens.
Compare to a .URL file opening a normal http: URI (handled by Edge):
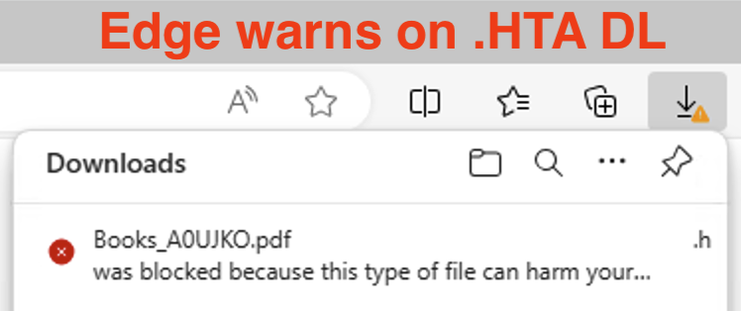
- Edge blocks downloading of .HTA files by default.
- If downloaded, the .HTA file has an explicit MotW, which enables:
- Smart App Control
- SmartScreen
Let's play a game and see if we can eliminate variables.
This time with no IE and no .URL files with mhtml: URIs, on a FULLY PATCHED (with July's patches) system. Sure, the file names still have BRAILLE PATTERN BLANK spaces for obfuscation, but that's mostly irrelevant.
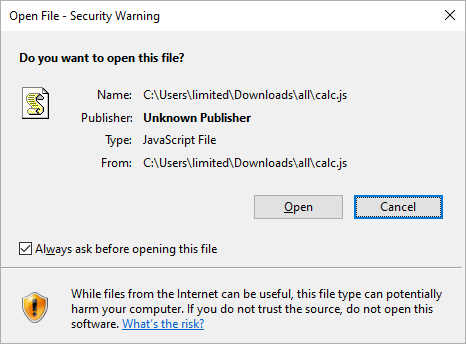
How does Windows handle .HTA files that are downloaded from the internet? A default Windows install with SmartScreen enabled will just open it without prompting. If we disable SmartScreen, we get a security warning before we can open it.
FWIW, This isn't the first time I've seen SmartScreen hurt Windows security as opposed to help it. (first time was CVE-2022-44698)
I have no idea about how anything works with SmartScreen behind the scenes. I'm just a curious observer of how Windows behaves. And what I'm observing here is that with .HTA files, SmartScreen makes Windows *less* secure. Am I missing something here?
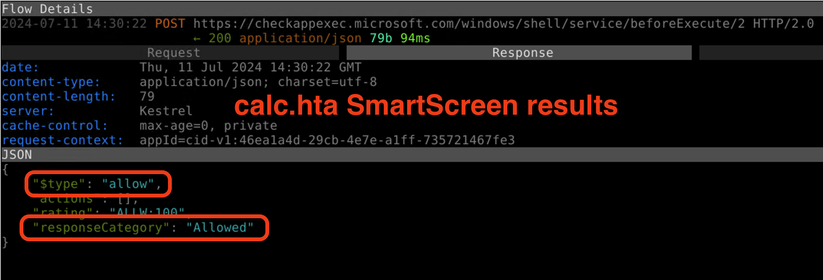
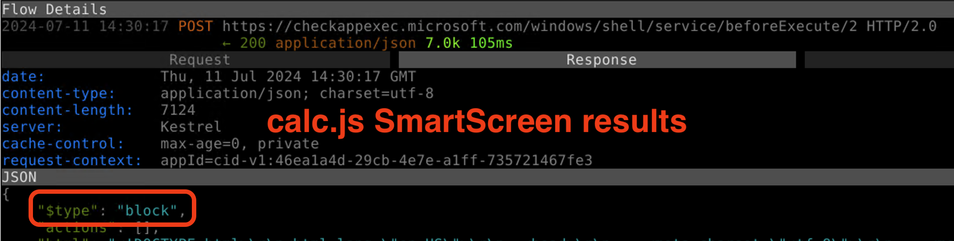
Just to be clear, SmartScreen *is* checking the .HTA file that is downloaded from the internet.
It's just that this .HTA file gets an "allow/Allowed" from SmartScreen, while another similarly dangerous .JS file returns "block/Untrusted"
The consequences of this is that the .HTA file runs and the MotW is stripped from the file when it is double-clicked, all automatically with no user interaction. The .JS file, on the other hand, warns the user and leaves it up to them to decide if it's worth the risk of running it.
I get that it's a laudable goal to have fewer security decisions for end users to make. However, for those of us who are better than average at making security decisions, it's an unpleasant surprise to have a system make a decision for you contrary to what you yourself would have decided.
Let's tie this all together.
With the CVE-2024-38112 exploit, the combination of a .URL file using an mhtml: URI triggers the invocation of Internet Explorer, which, in a mere THREE clicks from the user after clicking a file with a .pdf extension can end up in an HTA file executing.
Now that CVE-2024-38112 is patched, we cannot use IE by way of mhtml: in a .URL file anymore. So let's skip the URL/IE stuff and just put an HTA file in a ZIP. Surely Windows won't allow users to shoot this footgun easily, right?
ZERO clicks from clicking a file with a seemingly .pdf extension to end up with an HTA file executing. (on a system that has Smart Application Control disabled, such as an Enterprise Windows 11 system, or a Windows 10 system)
I get it that eliminating code flows that lead to IE is probably a good idea. But at least in the case of the attack outlined by Haifei at Check Point, the attack goes from three clicks (after file masquerading as a PDF is clicked) to zero clicks. The improvements with the patch is that the decoy HTA file can't have a PDF icon and won't indicate that it's an "Internet Shortcut" file, and also that SmartScreen will be involved, which seems fine to allow an HTA that pops calc.exe. The now-patched IE path invokes neither SAC nor SmartScreen in my testing.
@wdormann The design intent of SmartScreen AppRep is to suppress security warnings when nothing dangerous is happening.
Launching calc is not dangerous.
@tychotithonus I don't think I understand your proposal. The *whole point* of AppRep is to suppress security prompts when nothing bad is happening.
@Ericlaw Heh, maybe I'm missing the logical upshot, then.
If the described zero-click attack path can unexpectedly invoke an executable, could an AppRep false negative (something dangerous is happening, but AppRep thinks it's OK) produce a negative security outcome?
@tychotithonus Yes, if we decided "This is safe and we don't need to ask the human's opinion" that would be a bad outcome.
The challenge is that if you just "Always ask the human" no matter what the action is, the human is no longer reading/thinking and just starts blindly clicking "Run run run."